Instead of setting up a Wireguard VPN directly in my router I opted for the following setup:
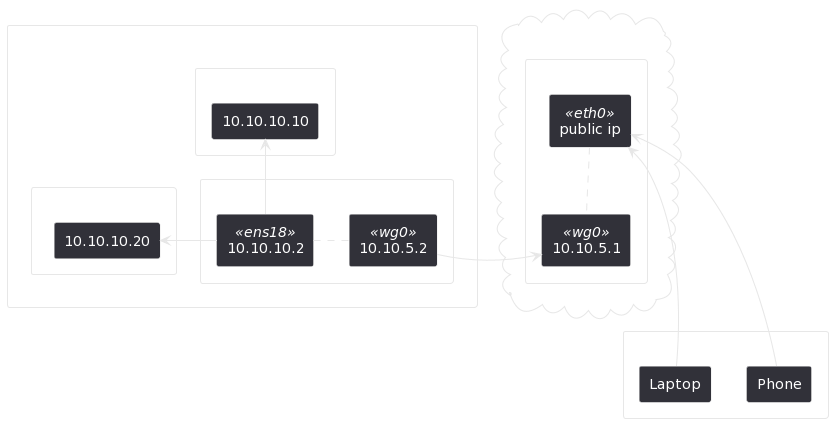
So instead of opening up ports on my router I will connect via Wireguard to a VPS hosted with Hetzner (which is called Jumpgate). In my local network I have an Ubuntu VM (called Wormhole) setup to connect to the Jumpgate and keep the connection active.
To achieve this I slightly adapted the example from the insdavm/WireGuard-site-to-site.md gist.
As both Jumpage and Wormhole are Ubuntu 22.04 VMs I simply installed wireguard using apt install wireguard. Besides that the only preparation on the VMs was activating net.ipv4.ip_forward=1 via sysctl.
Wormhole configuration
This is my wireguard configuration for Wormhole, obviously the parts containing the keys and endpoint need to be adapted.
[Interface]
Address = 10.10.5.2/24
PrivateKey = privkey
PostUp = iptables -A FORWARD -i %i -j ACCEPT
PostUp = iptables -t nat -A POSTROUTING -o ens18 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT
PostDown = iptables -t nat -D POSTROUTING -o ens18 -j MASQUERADE
# jumpgate
[Peer]
PublicKey = pubkey
Endpoint = jumpgate_public_ip_or_dns_name:51820
AllowedIPs = 10.10.5.1/24
PersistentKeepalive = 25
Jumpgate configuration
The configuration for Jumpgate looks very similar, again the parts containing the keys and endpoint need to be adapted.
[Interface]
Address = 10.10.5.1/24
PrivateKey = privkey
ListenPort = 51820
PostUp = iptables -A FORWARD -i %i -j ACCEPT
PostUp = iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT
PostDown = iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
# wormhole
[Peer]
PublicKey = pubkey
AllowedIPs = 10.10.5.2/32, 10.10.10.0/23
PersistentKeepalive = 25
# macbook
[Peer]
PublicKey = pubkey
AllowedIPs = 10.10.5.50/32
PersistentKeepalive = 25
# iphone
[Peer]
PublicKey = pubkey
AllowedIPs = 10.10.5.51/32
PersistentKeepalive = 25
Device config (Laptop, Phone, etc.)
To route all traffic through the VPN, I use this config:
[Interface]
PrivateKey = privkey
Address = 10.10.5.50/24
DNS = 10.10.5.1
[Peer]
PublicKey = pubkey
AllowedIPs = 0.0.0.0/0
Endpoint = jumpgate_public_ip_or_dns_name:51820
PersistentKeepalive = 25
To only route traffic to my internal network through the VPN, simply change the AllowedIPs in the Peer config:
[Interface]
PrivateKey = privkey
Address = 10.10.5.50/24
[Peer]
PublicKey = pubkey
AllowedIPs = 10.10.5.0/24, 10.10.10.0/23
Endpoint = jumpgate_public_ip_or_dns_name:51820
PersistentKeepalive = 25
